40 aws security best practices
What is AWS Security? Risks, Best Practices, and More Here are some best practices to help you choose the right solution: Easy integration. Choose a security solution that integrates with AWS to make the process painless. Maintain visibility and control. To be able to effectively audit and control compliance, choose a solution that allows total visibility and control. 50 AWS Security Tips To Secure Your Environment Basic AWS Security Practices — 1. Use the Advisor Tool. · 2. Categorize AWS assets. · 3. Design your company's Information Security Management System (ISMS).
9 AWS Security Best Practices - Alert Logic [ Data Security Best Practices] 6. Backup Your Data You never know if you're going to need to restore data after a breach, so back up your data regularly. You can do this by using AWS Backup. This app makes it easy to automate backups across your AWS environment, so you never have to worry about losing important information.
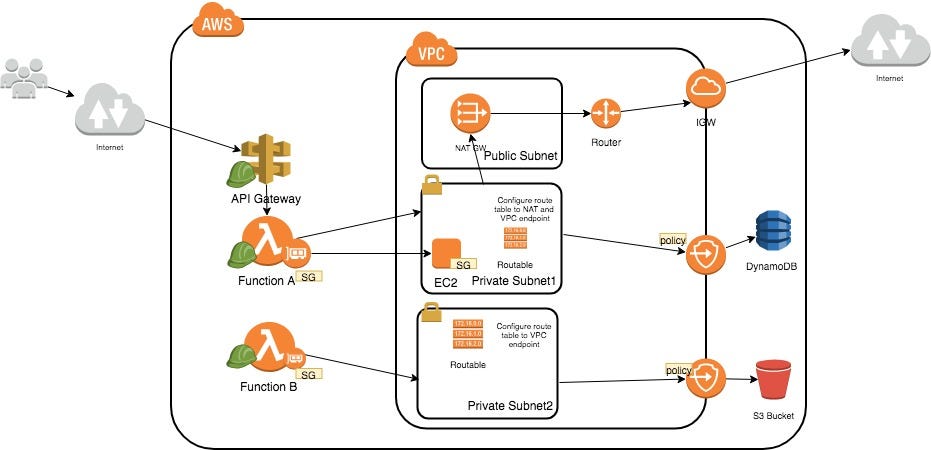
Aws security best practices
Aws network acl vs security group best practices jobs Search for jobs related to Aws network acl vs security group best practices or hire on the world's largest freelancing marketplace with 21m+ jobs. It's free to sign up and bid on jobs. AWS Security Best Practices | Cyphere - thecyphere.com Using security best practices helps businesses establish a security baseline and protect their AWS infrastructure from potential risks. By implementing these practices, companies can reduce the likelihood of data breaches, leaks, and other threats. Additionally, using security best practices can help businesses detect and respond to threats ... Best Practices | AWS Security Blog The AWS Security team has made it easier for you to find information and guidance on best practices for your cloud architecture. We're pleased to share the Best Practices for Security, Identity, & Compliance webpage of the new AWS Architecture Center.
Aws security best practices. 51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security. AWS Security Best Practices in 11 Steps - Apexon Most AWS services provide in-transit encryption by providing https endpoints that provide encryption end-to-end. AWS Certificate Manager allows you to create an SSL certificate for the public domain; Step 5: Follow Security Best Practices for AWS Database and Storage Services. RDS storage should be encrypted at rest. Security - AWS Well-Architected Framework Design Principles · Implement a strong identity foundation · Enable traceability · Apply security at all layers · Automate security best practices · Protect data in ... Amazon SNS security best practices AWS recommends that you use HTTPS instead of HTTP. When you use HTTPS, messages are automatically encrypted during transit, even if the SNS topic itself isn't encrypted. Without HTTPS, a network-based attacker can eavesdrop on network traffic or manipulate it using an attack such as man-in-the-middle.
PDF AWS Security Best Practices - AWS Whitepaper Title: AWS Security Best Practices - AWS Whitepaper Author: Amazon Web Services Created Date: 20220817200612Z AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices. Top 10 security best practices for securing backups in AWS If you leverage AWS Security Hub within your cloud environment, we recommend you enable the AWS Foundational Security Best Practices, as it includes detective controls that can help with securing backups in AWS. The detective controls in AWS Backup Audit Manager and Security Hub are also mostly available as AWS managed rules in AWS Config. AWS Tagging: Best Practices Chapter 11 - AWS Tagging: Best Practices. AWS tags are key-value pairs assigned to AWS resources as a form of additional data called metadata. Each tag is a user-defined or AWS-generated key and value assigned as a label against a resource. A tag is often attached to AWS resources to identify, categorize, organize, filter, or manage them.
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC. 21 AWS Security Groups Best Practices | McAfee Blog Definitive Guide to Securing Workloads on AWS Download to learn about the AWS adoption trends, security challenges and best practices around AWS and applications deployed in AWS. Download Now 6) Outbound access: Restrict outbound access from ports to required entities only, such as specific ports or specific destinations. 13 AWS IAM Best Practices for Security and Compliance 7) Set a regular cadence to review IAM permissions. As a security best practice, it's important to regularly review your organization's AWS IAM policies to ensure they're granting least privileges. Each policy comes with a policy summary, which is a good place to start when auditing IAM policies. AWS provides four levels of access for ... AWS Security Best Practices Checklist | CDWG Some practices may be as easy as performing regular data backups or creating appropriate password policies but can go a long way in increasing overall security. By following this checklist, you can help ensure that your cloud-based and in-house services are as secure as possible: 1. Create Strong Password Policies
AWS Security Best Practices Checklist - DZone Security AWS Cloud Security Best Practices. Tuning Redshift. The Top Ten Cloud Tools From AWS. AWS security Database Redshift (theory) cluster AI Data (computing) Virtual private cloud application ...
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion.
AWS Cloud Security Best Practices | CrowdStrike When defined, it should have a secure, hard-to-guess password, and it should be sent in an encrypted way for your third-party vendor to keep. To harden your security even more, you can rotate these external IDs once in a while. Keep Your Policies Simple, Small, and Scalable
AWS Security Best Practices | Classroom Training | AWS Students should have familiarity with AWS services and a strong background in information security concepts, techniques, and paradigms in the areas of networking, operating systems, data encryption, and operational controls. We recommend that attendees of this course have completed: AWS Security Fundamentals AWS Security Essentials Find a class
Top 10 Best AWS Security Practices | inVerita 10 AWS Security Best Practices #1 Learn How to Use the AWS Well-Architected Framework. Half the work is done if you have a clear grasp of your security job and duties in the shared responsibility model. Then among the first topics, you need to learn if you're just getting started with AWS would be Well-Architected Framework. This will assist ...
AWS Cloud Security: Best Practices for Financial Services It is possible to enhance AWS Cloud Security by just following a few security best practices defined below: 1. Establish an Effective Governance Strategy In a multi-cloud environment, utilize AWS Control Tower to build in security guardrails that enforce your organizational policies and remain in effect as you create new accounts or make ...
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ...
Best Practices - Security - Amazon Elastic Container Service Each topic in this guide starts with a brief overview, followed by a list of recommendations and best practices that you can use to secure your Amazon ECS clusters. Topics Shared responsibility model AWS Identity and Access Management Using IAM roles with Amazon ECS tasks Network security Secrets management
AWS Security Best Practices - CoreStack Learn the most important AWS Security Group best practices and follow step-by-step instructions and examples to configure them. Chapter 2 - S3 Security Learn the AWS S3 security principles of least privilege, access monitoring, encryption, and more, to protect against misconfiguration and data leakage. Chapter 3 - AWS NACL
Nine AWS Security Hub best practices | AWS Security Blog In this post, I'll provide nine best practices to help you use AWS Security Hub as effectively as possible. 1. Use the AWS Labs script to turn on Security Hub in all your AWS accounts in all regions and to establish your existing Amazon GuardDuty master/member hierarchy
Getting Started: Follow Security Best Practices as You Configure Your ... Following security best practices can help prevent your root account from being compromised, which is an important safeguard because your root account has access to all services and resources in your account. Create a strong password for your AWS resources
Best Practices | AWS Security Blog The AWS Security team has made it easier for you to find information and guidance on best practices for your cloud architecture. We're pleased to share the Best Practices for Security, Identity, & Compliance webpage of the new AWS Architecture Center.
AWS Security Best Practices | Cyphere - thecyphere.com Using security best practices helps businesses establish a security baseline and protect their AWS infrastructure from potential risks. By implementing these practices, companies can reduce the likelihood of data breaches, leaks, and other threats. Additionally, using security best practices can help businesses detect and respond to threats ...
Aws network acl vs security group best practices jobs Search for jobs related to Aws network acl vs security group best practices or hire on the world's largest freelancing marketplace with 21m+ jobs. It's free to sign up and bid on jobs.












0 Response to "40 aws security best practices"
Post a Comment